The 4 Pillars of Cryptographic Hygiene in the Post-Quantum Era
A pragmatic 2025 playbook for cryptographic hygiene: establish ownership and policy, continuously discover and inventory crypto across your estate, automate key and certificate lifecycl

The concept of “cryptographic hygiene” is evolving rapidly from a backend engineering concern to a boardroom priority. As Post-Quantum Cryptography (PQC) transitions from a theoretical future to an imminent reality, the fragility of legacy encryption presents a material business risk.
Recent data highlights the urgency: according to the 2025 IBM Quantum-Safe Readiness Index, the global average score for quantum readiness sits at just 25 out of 100, indicating that while awareness is growing, actual preparedness lags dangerously behind.
As with any robust Enterprise Risk Management (ERM) program, it’s essential to establish oversight of your enterprise’s cryptography, regularly assess risks, adapt processes for risk mediation, and have access to decision-useful data. For many organizations, this is a new frontier in Enterprise Risk Management (ERM) and compliance, but it follows the same logic as any other security discipline: you need visibility, governance, and consistent maintenance.
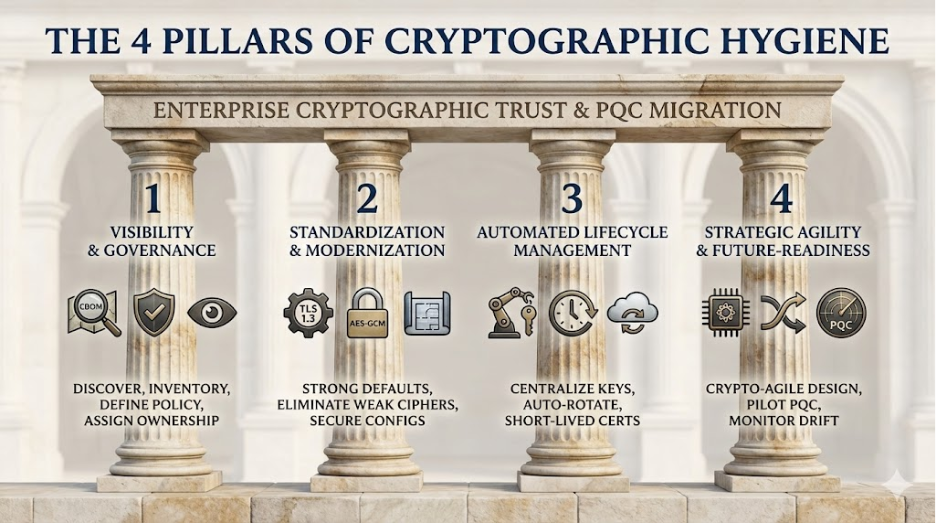
Pillar 1: Total Visibility and Governance
You can’t secure what you can’t see, and unfortunately most organizations don't understand just how much cryptography they rely on. The combination of shadow IT, legacy applications, and third-party libraries can become a landscape of unmanaged keys and certificates. In fact, a 2025 Trend Micro study found that 74% of organizations experienced security incidents specifically due to unknown or unmanaged assets.
Discovery and ownership form the foundation of cryptographic hygiene. Sufficient management of enterprise-wide cryptography requires transitioning from ad-hoc spreadsheets to establish a dynamic Cryptographic Bill of Materials (CBOM). The goal is to fingerprint everything: protocols (TLS/SSH), cipher suites, key lengths, and certificate chains. This inventory must map data flows to identify where sensitive data is in transit and at rest, linking specific crypto controls to your data classification policies.
Cryptography governance is non-negotiable and helps secure ongoing ROI from cryptographic visibility projects. Consider your organization’s other governance structures as a blueprint: assign clear ownership for cryptography, such as a cross-functional group involving security architecture, platform engineering, and application teams. These owners are responsible for defining the policy (e.g., approved algorithms, rotation periods, exception handling), supporting regulatory compliance, and monitoring existing and emerging risks.
Pillar 2: Standardization and Modernization
Once you’ve inventoried your organization’s cryptography, it's important to standardize the management of this function. This pillar focuses on eliminating weak links by enforcing strong, modern defaults across the enterprise.
This starts with clearly defining algorithms and parameters. For transport, this means mandating TLS 1.2 or higher (preferring 1.3) and disabling deprecated options like NULL, RC4, 3DES, or SHA-1. For data at rest, organizations should standardize authenticated encryption modes (like AES-GCM) with appropriate key lengths.
It is best practice to extend this standardization to the software supply chain. Developers shouldn’t write their own crypto or hard-coding secrets. Instead, enforce the use of vetted, standard libraries and secrets managers that inject credentials at runtime. By mandating encryption and signing templates and gating deployments that introduce deprecated ciphers, you can prevent poor cryptographic hygiene from impacting production.
Pillar 3: Automated Lifecycle Management
Most certificate outages and key compromises are caused by human error. Often, someone forgets to renew a certificate or mishandles a key. The scale of this problem is massive: CyberArk’s 2025 State of Machine Identity Security Report notes that 79% of organizations expect the number of machine identities to grow by up to 150% in the coming year, yet nearly 80% of companies still experienced a certificate-related outage in the last 12 months.
It’s important to think of keys and certificates as living objects with their own lifecycles. They are created, used, rotated, and eventually revoked. Effective management depends on centralizing keys in a Key Management Service (KMS) or Hardware Security Module (HSM), thereby strictly avoiding app-embedded keys.
Certificate and key rotation should be automated and frequent. If you are manually renewing certificates, you are already behind —especially with certificate lifespans predicted to shrink to just 47 days by 2029. Leveraging protocols like ACME for automated issuance and renewal eliminates the "surprise expiry" that causes delays and poses risks. Furthermore, enforcing short-lived certificates can help reduce the scale of an attack.
Pillar 4: Strategic Agility and Future Readiness
The final pillar focuses on “futureproofing" your cryptography by staying up to date on risk factors, solutions, and emerging regulations. The transition to Post-Quantum Cryptography (PQC) is not a simple occasional update. Rather, it is a fundamental migration of trust infrastructure.
According to a 2024 Ponemon Institute study, while 61% of organizations plan to migrate to PQC within five years, 27% have not even started preparing. Static security posture is already outdated. Systems must be designed with crypto-agility in mind so that algorithms and keys can be swapped without rewriting applications or redesigning the architecture. Organizations should begin piloting PQC in non-critical paths today (such as hybrid key exchange in TLS) to understand the performance and interoperability impacts.
Monitoring and response processes must also be agile. Ideally, your security operations center (SOC) will leverage dashboards that alert on "crypto drift", such as unexpected protocol downgrades or the sudden appearance of weak ciphers. If a Certificate authority is breached or an algorithm is suddenly declared vulnerable, your teams need an Incident Response playbook specifically designed to swiftly handle cryptographic remediation.
CISO Takeaway
Investing in these pillars delivers immediate ROI beyond just "compliance."
- Reduced Operational Risk: You eliminate the fire drills caused by surprise certificate expirations.
- Reduced Compromised Assets: Centralized key control and short-lived credentials limit what an attacker can do if they get inside.
- Audit Readiness: Clear policies and traceability make SOC 2 and ISO audits faster and less painful.
Most importantly, a risk-prevention approach can help shift the likelihood of investing significant resources in remediation. Waiting to prepare for the post-quantum transition may result in skyrocketing costs, regulatory non-compliance fines, and strain on internal resources.
Don’t forget your Cryptographic Bill of Materials (CBOM)
Qinsight helps security teams move from ad-hoc crypto management to continuous cryptographic posture management—providing the visibility and automation required to reduce outages today and prepare for post-quantum risk tomorrow.

Subscribe to our weekly newsletter
Receive weekly insights on cryptographic risks, emerging security standards and quantum readiness.



