Cryptographic Discovery
Qinsight automates discovery so teams can eliminate blind spots and understand the true footprint of their cryptography.
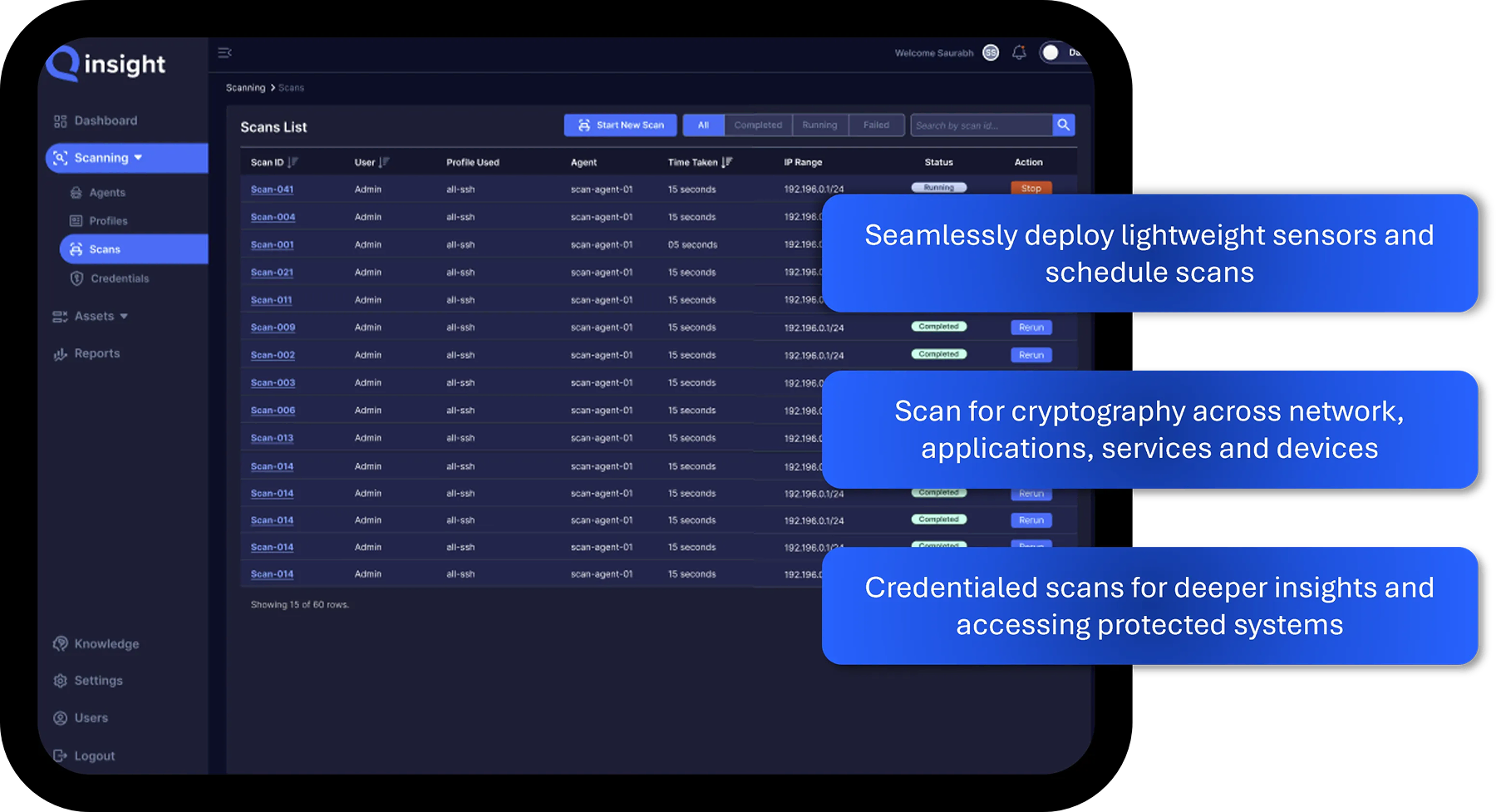
Scale and Automate The Cryptographic Discovery Process
Discover cryptographic assets across the network, infrastructure and applications with Qinsight Atlas' multi-pronged scanning approach. Deploy sensors to monitor cryptography in network segments and scan applications and services with credentialed scans.
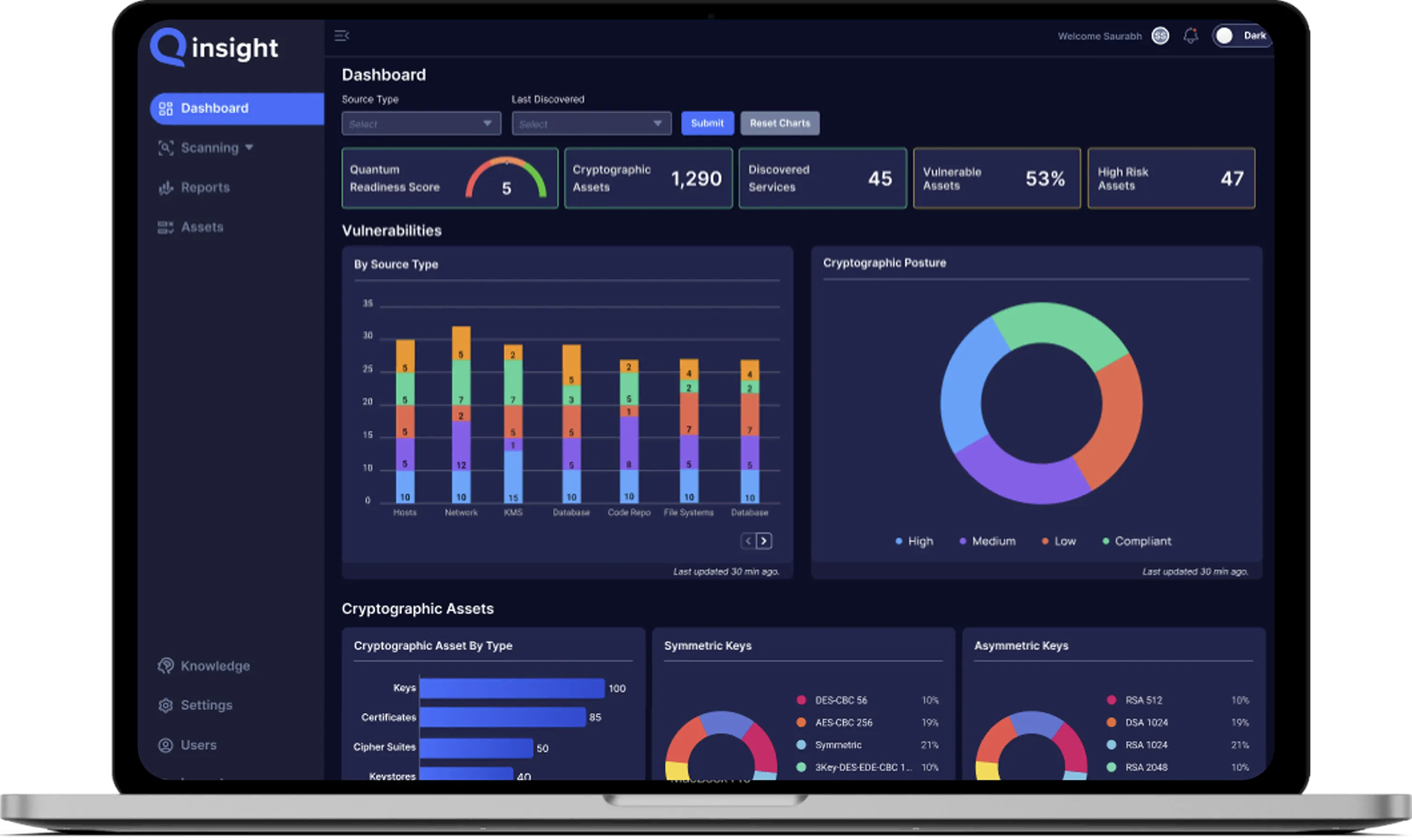
Improve Cryptographic Posture
Fully Visibility
Gain complete insight into all cryptographic assets across your enterprise environment.
Continuous Monitoring
Detect changes in cryptography in real-time to maintain ongoing protection and compliance.
Improve Security
Identify weak or expired encryption, keys, and certificates before they become exploitable.
Reduce Downtime
Prevent service outages by proactively managing expiring ceritifcates and crypto dependencies
Quantum Readiness
Assess exposures to quantum-vulnerable algorithms and plan migration to post-quantum standards.
Ensure Compliance
Meet evolving regulatory and industry mandates through automated crypto audits and reporting.
How Qinsight Atlas Discovery Process Works
Two step discovery process to ensure maximum reach and depth of insights across data sources.

Deploy Sensors Across Network Segments
Deploy sensors either directly or through a proxy connection within each network segment. Collect network cryptography and discover applications and services where credentialed scans are necessary.

Connect to Source Types and Add Credentials
Findings are normalized into a searchable CBOM with algorithms, key sizes, certificate chains/issuers/expirations, protocol/cipher details, systems, and owners — ready to tag and export.
Schedule Scans for Continuous Monitoring
Policy checks flag weak/expired/non-standard crypto, deprecated protocols, short keys, and quantum-susceptible usage. Get a PQC readiness score, and export compliance-ready reports (CSF 2.0, DORA, NIS2).
