PQC Migration Steps & Best Practices for Organizations (with NIST CSWP as your North Star)
NIST-aligned playbook for PQC migration: build HNDL registry, automate crypto inventory and CBOM, modernize PKI, pilot hybrids, attest quarterly. now.

Post-quantum cryptography (PQC) is no longer theoretical—it is an urgent, multi-year transformation that touches governance, architecture, supply chain, PKI, and operations. Below is a practical, step-by-step playbook you can use to plan and execute your migration, anchored to NIST’s Cybersecurity White Paper (CSWP) mapping PQC migration capabilities to the Cybersecurity Framework (CSF) 2.0 and SP 800-53 controls.
0) Pre-work: Build a “Harvest-Now-Decrypt-Later” (HNDL) registry
Before you begin the process of inventorying your cryptographic assets, determine which assets are most sensitive to HNDL. Ask yourself: "which assets would be most harmful if they were able to be decrypted by bad actors 5-10 or 15 years down the line?" Prioritize upgrading the encryption of these assets during your PQC migration process.
What to do
- Define HNDL criteria: datasets needing confidentiality ≥ 5–10 years (health records, PII, trade secrets, long-life contracts, IP, defense adjacencies).
- Register HNDL systems: tie datasets to apps, services, certificates, keys, and owners.
- Tag in inventory: ensure HNDL labels propagate to assets/keys so they rise to the top during prioritization.
Outcome: Clear, objective inputs for risk scoring and migration waves.

1) Establish program governance and define your “why”
Create an executive-sponsored PQC program that sets scope, risk appetite (including HNDL exposure), decision rights, and success metrics. Create a cross-functional team to lead the initiave, ensuring team members have the necessary capabilities to spearhead this initiave. Ask yourself if there is sufficient internal expertise or if external consultants are needed to fill knowledge gaps and introduce structure. The NIST CSWP frames PQC migration as a capability set integrated with CSF 2.0 and SP 800-53—not a one-off project.
Decision rights to formalize (critical)
- Algorithm allow-lists / block-lists (classical & PQC; hybrids for Tier-0).
- Exception handling (time-bound, owner-approved, with remediation plans).
- Vendor approvals (PQC roadmaps, SBOM/CBOM requirements, contract milestones).
Best practices
- Charter a cross-functional working group (security architecture, PKI/KMS, platform, networking, SRE, procurement, legal).
- Use CSF 2.0 outcomes as the program’s language; map tasks to SP 800-53 controls for auditability.
2) Build a cryptographic inventory—automated, complete, and continuous
You can’t migrate what you can’t see. NIST elevates discovery/inventory as the starting capability: scanning code and CI/CD, binaries, services/protocols (TLS/SSH/QUIC), endpoints/servers, keystores, PKI, and HSMs—then correlating with existing hardware/software inventories.
Don’t forget these common blind spots
- Private APIs & service meshes (mTLS), sidecar-to-sidecar traffic.
- Proxies/load balancers and TLS termination points.
- IoT/OT gateways, message buses, and internal RPC.
- API gateways and internal developer platforms.
Best practices
- Automate discovery across code (SCA/IDE hooks), binaries, and live services; include certificate stores and API gateways.
- Normalize results into a single inventory, tagging algorithm, key lengths, protocol config, certificate attributes, HNDL flags, and owners.
- Treat certificates & keystores as first-class assets with lifecycle management.
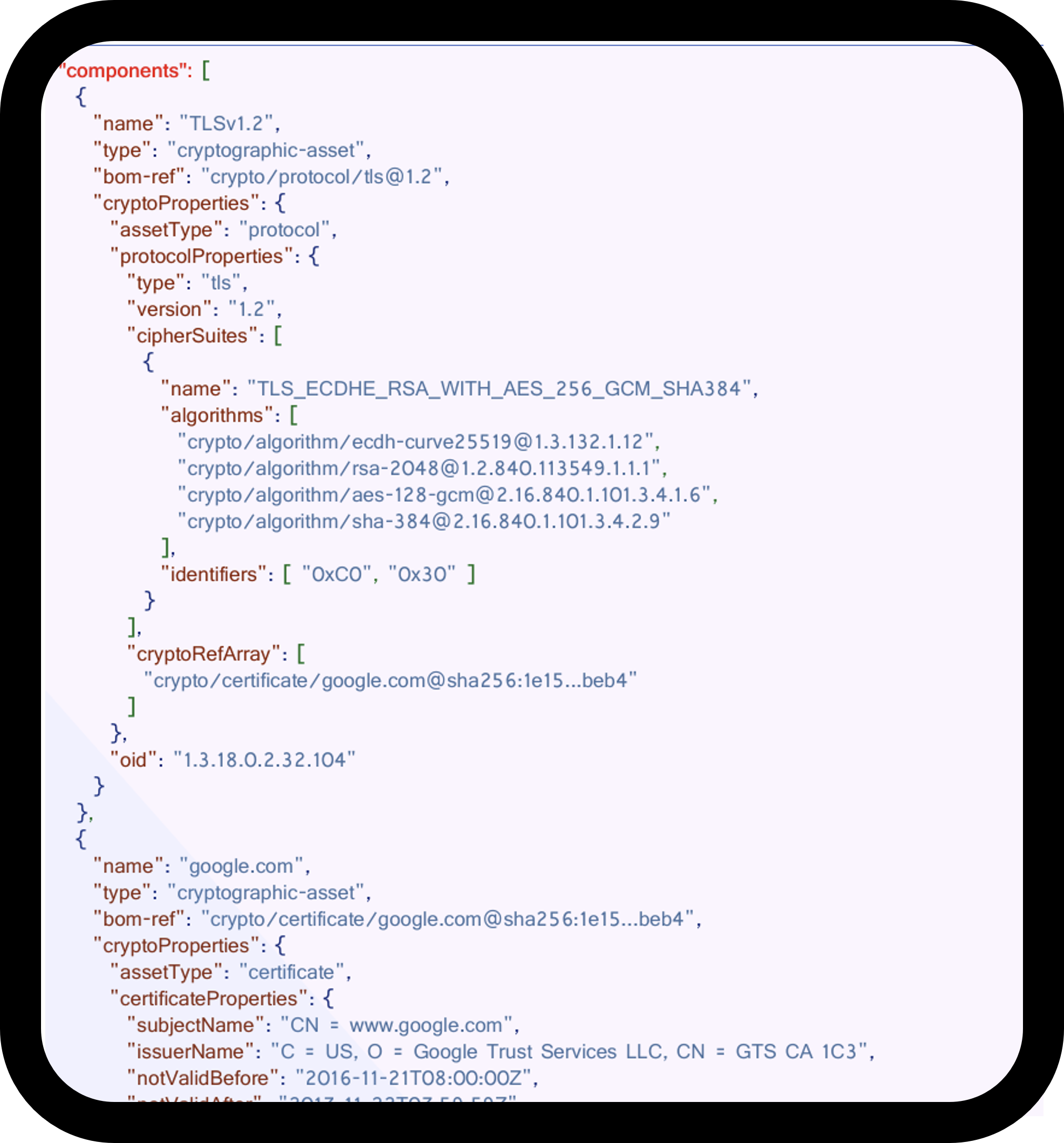
3) Represent crypto assets with a CBOM for scale and transparency
Adopt a Cryptographic Bill of Materials (CBOM) (e.g., CycloneDX) to model algorithms, keys, protocols, and certificates—including properties and dependencies—so you can reason about posture, enforce policy, and exchange machine-readable evidence with vendors.
Concrete policy example
- CI/CD gate: Block merges if CBOM includes RSA-1024, SHA-1, MD5, or non-NIST PQC algorithms.
Best practices
- Issue CBOMs for critical apps/services; require CBOM/SBOM from suppliers.
- Use CBOM metadata (algorithm variant, key size, cert validity, OIDs) to drive policy gates.
4) Quantify quantum risk and prioritize migration
With inventory in hand, perform risk triage supported by cryptographic analytics.
Simple, actionable scoring model
- Risk Score = Confidentiality Lifetime (1–5) × Exposure/Blast Radius (1–5) × Migration Difficulty (reverse 1–5)
- Confidentiality Lifetime uses your HNDL registry.
- Exposure includes roots of trust, firmware signing, PKI hierarchy, internet exposure.
- Migration Difficulty considers performance constraints, vendor readiness, protocol limits.
Define migration waves
- Tier-0: roots of trust, PKI/CA, HSM/KMS, firmware signing.
- Tier-1: external-facing TLS, VPN, admin access.
- Tier-2: internal services, IoT/OT, messaging, service mesh.
5) Engage suppliers and align the cryptographic supply chain
Discovery and inventory are prerequisites for third-party risk management. Require vendor roadmaps for PQC support, demand SBOM/CBOM, and assess managed services, cloud KMS/HSMs, and CAs for PQC/hybrid readiness.
Best practices
- Bake CBOM/SBOM + PQC milestones into contracts and renewal clauses.
- Ask CAs/HSM/KMS providers about supported key types, hybrid certificate formats, chain size limits, and performance.
6) Design for crypto agility—make switching algorithms routine
PQC won’t be one-and-done. Build algorithm agility into protocols, libraries, and services: version negotiation, feature flags, dual-stack/hybrid operation, and policy-driven selection.
Program guardrails (copy-pasteable)
- Algorithm policy: Only NIST-recommended PQC (e.g., ML-KEM/ML-DSA) and CNSA 2.0-aligned classical suites; hybrids required for Tier-0 until cutover.
- Key-lifetime policy: Max 12 months for server certs; rotate signing keys on compromise or policy change; enforce via CI/CD gates.
- Exception policy: Time-boxed, with business owner sign-off and a dated remediation plan.
- Feature-flag rollouts: Enable PQC by tenant/region/endpoint class, with automated rollback.
7) Modernize PKI and key management early
X.509 profiles, CA software, OCSP/CRL infra, and HSM/KMS boundaries need updates for PQC key types and larger artifacts. Plan for certificate renewal at PQC scale.
Specific risks to validate
- Path MTU & header size with hybrid certificates (ClientHello and certificate chain sizes).
- OCSP stapling behavior with larger chains and middleboxes.
- Chain length and intermediate size limits across clients, proxies, and load balancers.
Best practices
- Validate CA path for PQC/hybrid support, chain size limits, and policy OIDs.
- Confirm HSM/KMS support for target key types & lifetimes; test backup/restore, wrap/unwrap, and signing throughput with PQC.
8) Pilot interoperability & performance in a lab before production
Use a lab to validate compatibility and performance across TLS, QUIC, SSH—plus HSMs, CAs, and middleboxes.
Interop & performance test matrix (ready to use)
- Protocols: TLS 1.3, QUIC, SSH.
- Artifacts: classical, hybrid (KEM + signature), pure PQC (where supported).
- Vendors: CAs, HSMs/KMS, load balancers, API gateways, service mesh.
- Middleboxes: WAF, DLP, IDS/IPS, TLS inspection/termination.
- Metrics: handshake bytes, CPU, p95 latency, error codes, path-MTU, cert chain size, OCSP stapling success.
- Fail modes: version downgrade, suite mismatch, “client hello too large,” stale/oversized stapled OCSP, MTU fragmentation.
Best practices
- Re-run functional and perf tests for each protocol/library update; include failure/fallback paths.
- Capture baselines and SLOs per service to negotiate acceptable overhead.
9) Execute phased rollouts with guardrails
Start with low-risk, high-visibility paths (internal admin channels, selected external endpoints) using hybrid KEM/signature where feasible. Use canaries, progressive exposure, and automated rollback tied to crypto health signals (handshake success rate, error codes, latency regressions).
Best practices
- Maintain dual issuance (classic + PQC/hybrid) during transition windows.
- Gate promotions on objective acceptance criteria and observability dashboards.
10) Operate, attest, and audit continuously
Keep discovery and analytics always on to catch drift, non-compliant configs, and expired/weak certs.
Attestation cadence
- Quarterly CBOM attestations for Tier-0/Tier-1; semi-annual for lower tiers.
- KPIs to track: % assets inventoried; % Tier-0 migrated; % services hybrid-enabled; certificate PQC coverage; mean time to replace vulnerable crypto.
- Integrate crypto posture into incident response and contingency plans.
Common pitfalls to avoid
- Inventory blind spots (embedded/IoT, private APIs, service mesh mTLS, legacy middleware). Fix with targeted sensors and vendor CBOMs.
- PKI edge cases (certificate size, intermediates, path length, OCSP stapling). Prototype with real chains and clients.
- Assuming drop-in replacement—PQC has different size/performance profiles; expect tuning and architectural adjustments.
- Monitoring gaps—APM often ignores handshake size/latency; add crypto-specific SLOs.
30-60-90 day starter plan (program-manager edition)
Days 0–30
- Program charter & decision rights set; HNDL registry v1 complete.
- Initial agentless discovery; CBOM schema chosen; vendor questionnaire drafted.
Days 31–60
- Full crypto inventory; first risk triage & migration waves; lab stood up.
- PKI readout (chain length/OIDs/OCSP); exception process live.
Days 61–90
- Hybrid pilots for TLS/SSH in canary; CI/CD CBOM gate “warn → block.”
- KPI dashboard live; quarterly attestation schedule set.
How Qinsight Can Help: Cryptographic Discovery, Inventory & Posture Management

Discovery and inventory are the first critical steps in the PQC migration process. Qinsight Atlas is a cryptographic discovery, inventory, and analytics platform built to operationalize the exact capabilities NIST highlights—agentless scanning across TLS/SSH, databases, APIs, CI/CD, cloud, IoT devices and more; classification of vulnerable algorithms; CBOM generation; and policy-driven prioritization and remediation. Our guidance and defaults are aligned to NIST CSF 2.0, SP 800-53, and NSA CNSA 2.0, and remediation recommends only NIST-approved PQC algorithms.
Qinsight can produce a CBOM-backed crypto inventory and PQC risk heatmap in days, mapped to CSF 2.0/SP 800-53.
Ask for a pilot: we’ll scan a defined scope, deliver your Tier-0/Tier-1 migration plan, and set up CI/CD policy gates.
Ready to see your crypto posture—everywhere it lives—and plan your PQC migration with confidence? Reach out to Qinsight to start your assessment today.
FAQ: Post-Quantum Cryptography Migration
1. What is post-quantum cryptography (PQC)?
Post-quantum cryptography refers to cryptographic algorithms designed to remain secure against attacks by quantum computers, which can break classical encryption like RSA and ECC using Shor’s algorithm.
2. What does “Harvest Now, Decrypt Later” mean?
It describes a threat where attackers steal and store encrypted data today, planning to decrypt it later once quantum computers become powerful enough to break current encryption standards.
3. Which encryption algorithms are quantum-vulnerable?
RSA, DSA, Diffie-Hellman (DH), Elliptic Curve Diffie-Hellman (ECDH), and Elliptic Curve Digital Signature Algorithm (ECDSA) are all vulnerable to quantum attacks.
4. What are NIST-approved post-quantum algorithms?
NIST has standardized ML-KEM (Kyber), ML-DSA (Dilithium), and SLH-DSA (SPHINCS+) for PQC, with FN-DSA (Falcon) and HQC as upcoming additions. LMS and XMSS are also approved for specialized use cases.
5. What is a CBOM and why does it matter?
A Cryptographic Bill of Materials (CBOM) lists all cryptographic assets—algorithms, keys, and certificates—used in an application. It helps organizations visualize, manage, and validate cryptographic posture during PQC migration.
6. How should organizations start PQC migration?
Follow NIST CSWP guidance: build an HNDL registry, automate crypto discovery, represent assets as CBOMs, modernize PKI, pilot hybrid algorithms, and track migration progress with continuous attestation.
Subscribe to our weekly newsletter
Lorem ipsum dolor sit amet consectetur. Lacus id turpis ut nulla dui proin nunc.


.png)