The Looming Quantum Threat
Quantum computers aren’t theoretical anymore — their capabilities are progressing fast, and the consequences for cybersecurity are severe. Public-key cryptography as we know it will be broken. That includes RSA, Elliptic Curve, and Diffie-Hellman — the algorithms that power TLS, VPNs, digital signatures, and more. But the threat isn’t just the future quantum machine. The real danger is happening right now.
Harvest Now, Decrypt Later is Real
Adversaries — especially nation-states — are already intercepting and storing encrypted data. Their plan? Decrypt it once quantum computers are powerful enough. If your data has long-term value (financial, health, legal, government), it’s already at risk.
Types of Quantum Attacks
Integrity and Data Authentication Risks
Many systems rely on digital signatures to verify that data hasn’t been altered. When those schemes break, attackers can manipulate or spoof data — without detection.


Harvest Now, Decrypt Later (HNDL)
Attackers capture encrypted traffic today, assuming they’ll decrypt it later. This is especially dangerous for:
- Financial and healthcare data (PII)
- Intellectual property
- Government and military communications

Active Attacks on Digital Signatures
Quantum computers will break the math behind RSA and ECDSA. This means attackers can:
- Forge digital signatures
- Impersonate users
- Break the trust layer of your authentication systems
What’s Vulnerable
Public-Key Cryptography (Most At Risk)
Will be fully broken by Shor’s Algorithm:
- RSA
- Elliptic Curve (ECDH, ECDSA)
- Diffie-Hellman
These algorithms are secure
- TLS (SSL)
- VPNs
- Digital certificates
- Code signing
- Identity verification
Symmetric-Key Cryptography (Still Viable)
Algorithms like AES, SHA-2, and HMAC are more resilient. Grover’s Algorithm weakens them, but only partially — doubling key sizes is typically enough. However, key exchange mechanisms still rely on vulnerable public-key crypto — meaning symmetric encryption is only safe after secure key exchange has occurred.
What is Quantum Secure Cryptography?
Post-Quantum Cryptography (PQC) refers to new cryptographic algorithms designed to withstand quantum attacks.
Led by NIST, the PQC standardization process selected algorithms like
- Kyber (key exchange)
- Dilithium, Falcon (signatures)
The future will involve
- Gradual rollout of hybrid systems
- Long transition periods
- Vendor and protocol upgrades
But none of that matters if you don’t know what you’re using today.
Why Act Now?
The first step isn’t migration, it’s visibility — knowing where cryptographic risk exists in your environment.
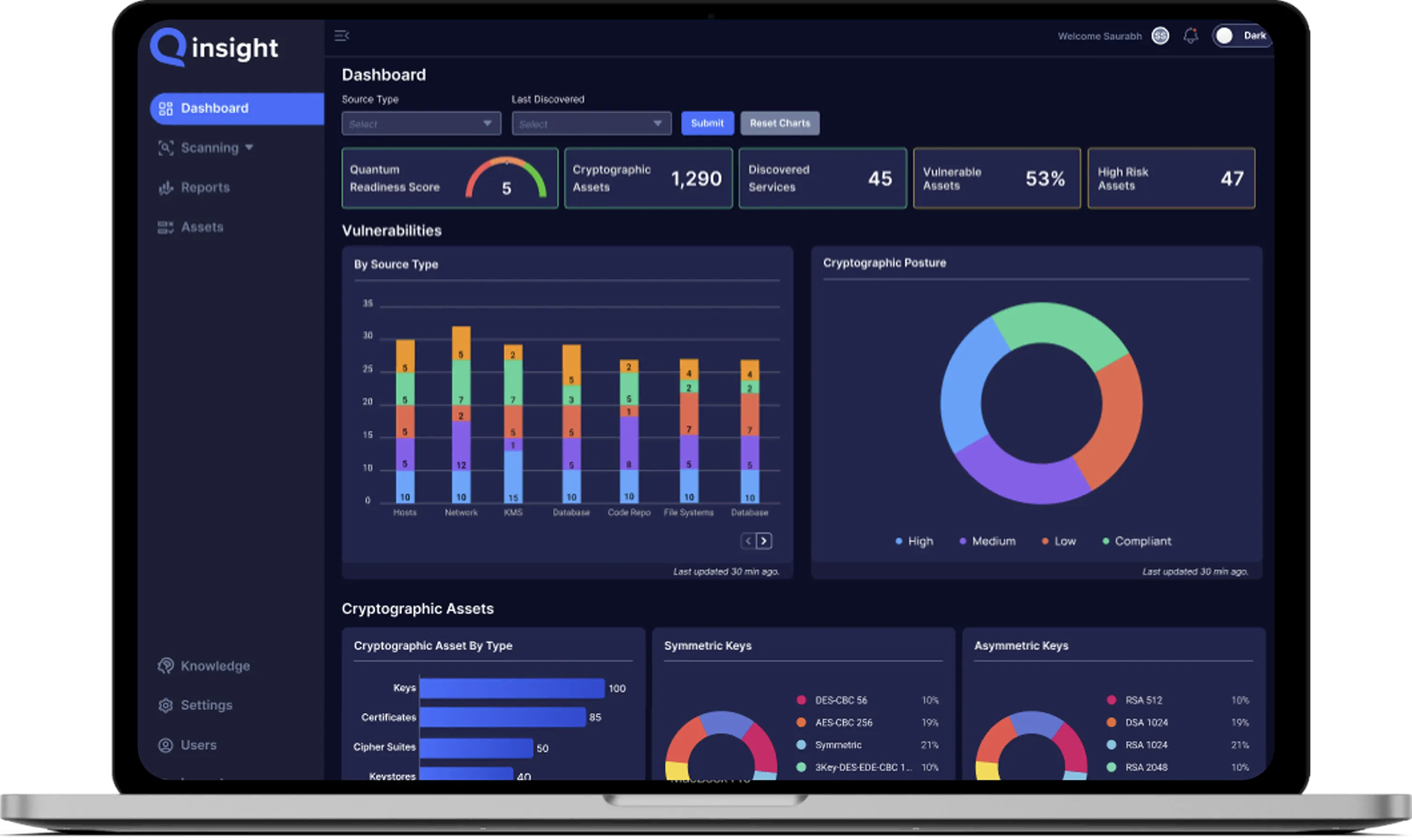
How Qinsight Helps
Qinsight is a cryptographic posture management platform that helps you
- Discover where and how encryption is used across TLS, SSH, and certificates
- Analyze what algorithms are in use and whether they’re quantum-vulnerable
- Act on prioritized guidance to remediate outdated cryptography
- Align with NIST, PCI-DSS, and post-quantum migration requirementsWhether you’re starting your quantum readiness journey or validating your existing posture, Qinsight gives you the visibility and insights to act — before it’s too late.