Qinsight Atlas Cryptographic Discovery & Posture Management
The only platform that discovers, inventories, and enriches cryptographic assets with business context — so you can fix what matters.
Cryptographic Posture Management Platform Built for the Post-Quantum Era
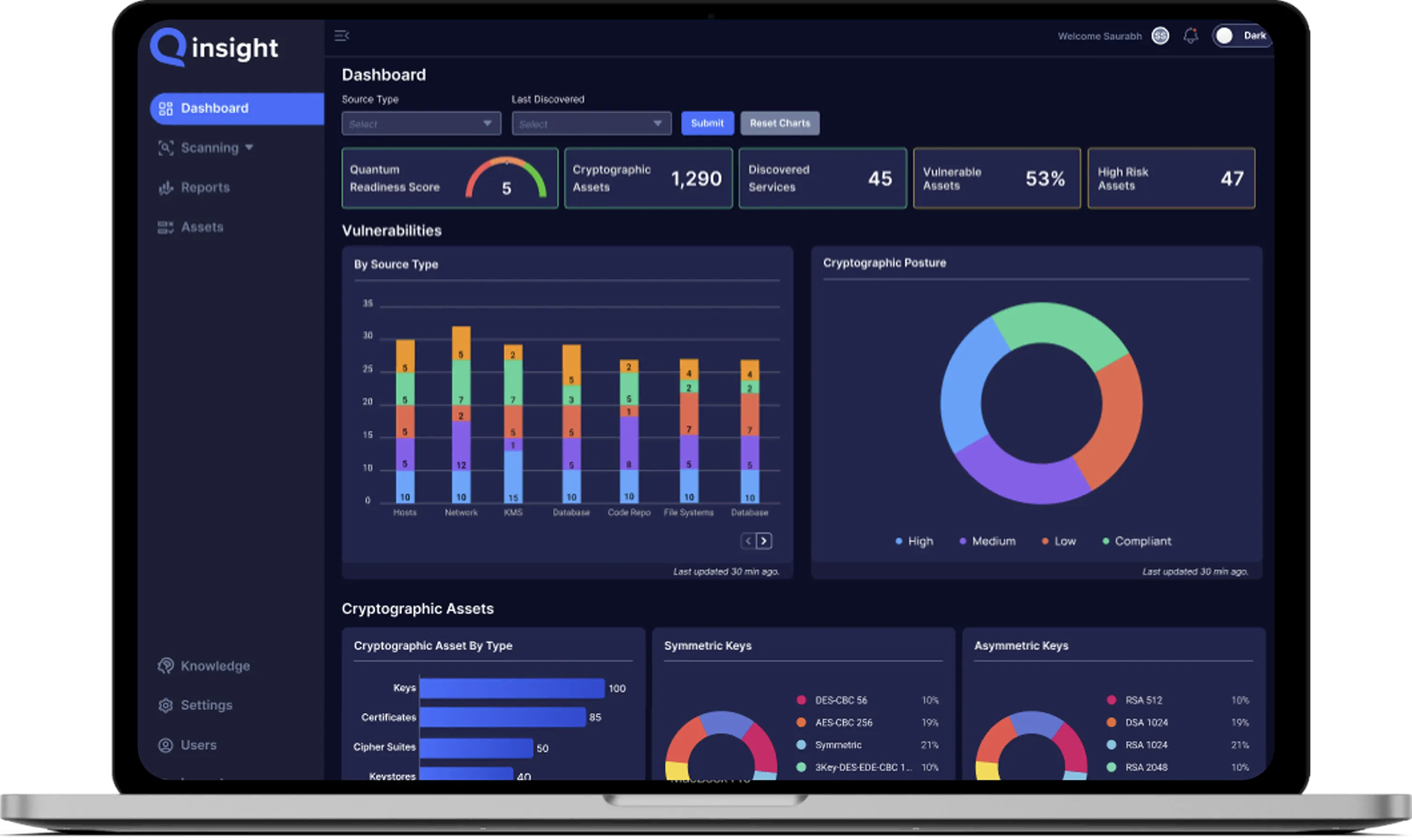
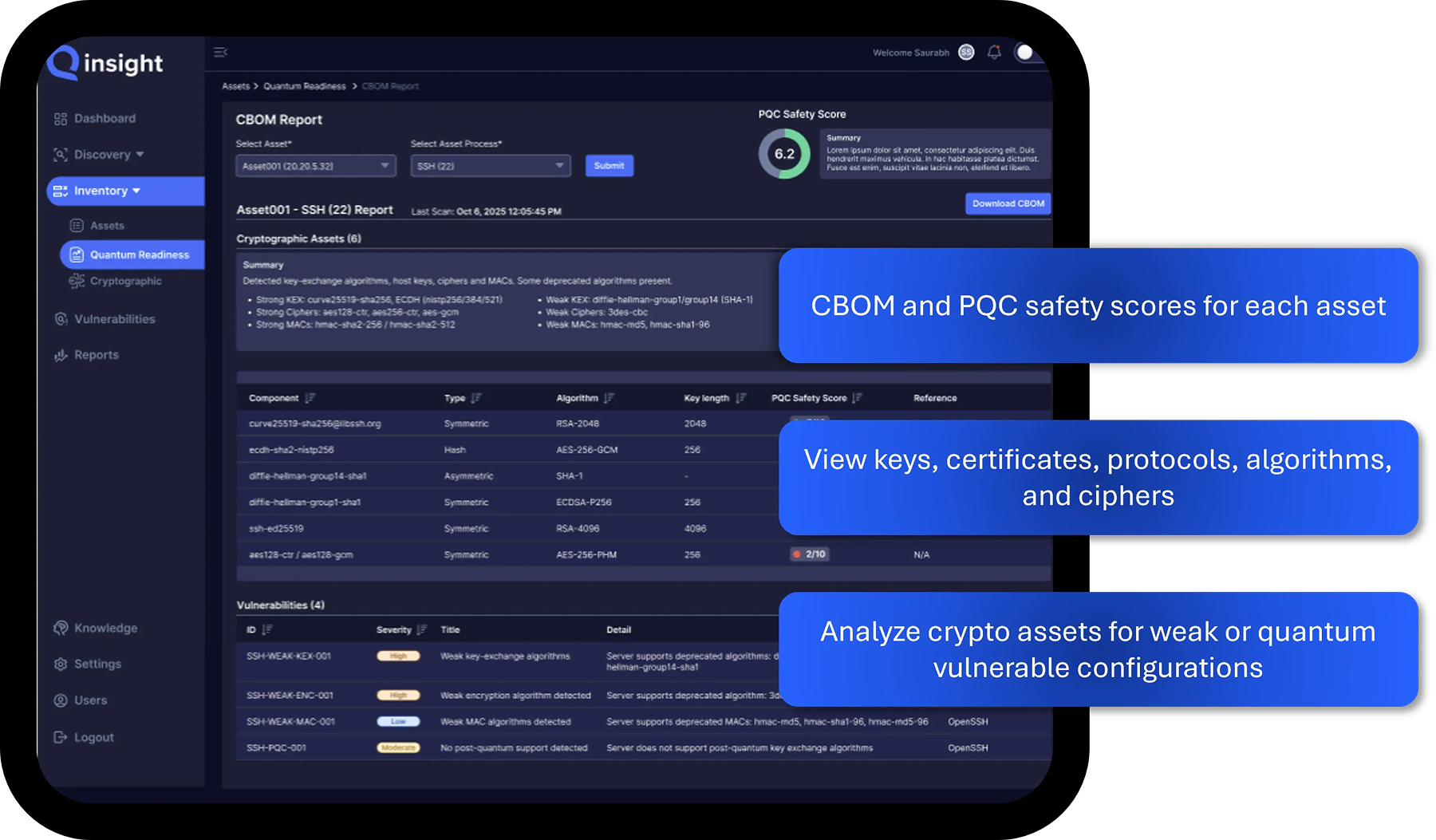
Qinsight helps you discover, inventory, analyze, and act on all enterprise cryptography in one place. It builds a living catalog (CBOM) of keys, keystores, certificates, algorithms, protocols, and libraries. Risk engine flags weak / quantum-vulnerable assets or non-compliant crypto and provides remediation guidance to improve cryptographic posture and quantum readiness.
The Complete Cryptographic Posture Management Platform

Automated Discovery
Uncover deep-seated cryptography across cloud, code, and endpoints using lightweight sensors and API integrations.

Dynamic Crypto Inventory
Transform scattered metadata into a unified, dynamic Cryptographic Bill of Materials (CBOM) for each source scanned.
Enrichment & Risk Assessment
Turn raw inventory into actionable intelligence by correlating findings with CMDB context. Flag both classical and post-quantum risks in real-time.
Remediation & Compliance
Drive action with prioritized remediation guidance and generate audit-ready reports to demonstrate compliance.
Qinsight Atlas Platform

Qinsight Atlas Features
Cryptographic Discovery & Inventory
Network and credentialed scans cover IT and OT infrastructure and inventory cryptographic algorithms, ciphers, protocols, libraries, keystores and certificates within a CBOM.
Compliance Dashboards & Reporting
Built-in reports and dashboards map findings to frameworks like NIST PQC guidance and CBOM-style inventories for streamlined reporting and audits.
Analytics & PQC Risk Assessment
Qinsight classifies algorithms and flags what’s “at risk” vs. PQC-ready so teams can see exposure at a glance.
Open Integrations & Connectivity
A REST API and advanced integrations (e.g., AWS KMS, Azure Key Vault) let Qinsight plug into existing workflows, SIEMs and key infrastructure.
Continuous Monitoring & Scheduled Scans
Beyond one-off checks, the platform supports daily/continuous discovery and scheduled scans.
Guided Remediation Workflows
Fixes are prioritized by severity and provides guided PQC migration/remediation paths to accelerate algorithm swaps at scale.
Who Needs a Cryptographic Posture Management Platform?
CISOs and Security Architects
Get instant visibility into where encryption lives, a clear PQC-risk view, and posture scoring so you can prioritize migrations, justify spend, and show progress to the board.
Crypto Governance Teams
Maintain a living inventory of algorithms and certificates, track key/cert lifecycles, and use guided crypto-agility workflows and APIs to drive consistent, scalable remediation.
Compliance, risk and InfraSec leaders
Produce audit-ready reports and dashboards mapped to NIST PQC guidance, with continuous monitoring and audit logs that embed smoothly into existing compliance workflows.

// Why Now //
Why Post-Quantum Readiness Can't Wait
A cryptographic inventory is quickly becoming table stakes for PQC migration and compliance. With HNDL, adversaries can harvest today and decrypt tomorrow—organizations must act now to protect their cryptographic estate.

Harvest Now, Decrypt Later Threat
Nation-state actors and sophisticated adversaries are already intercepting and storing encrypted data today with the intent to decrypt it once quantum computers are capable of running Shor's algorithm.

Compliance Requirements
NIST has finalized post-quantum algorithms, and regulations are emerging that will require organizations to discover, inventory and assess their cryptographic assets to ensure they are compliant.
// Get in touch //
Ready to secure yourself for the quantum era?
Let's start with visibility.


