Cryptographic Risk Assessment
Analyze Post-Quantum Risks and Protect Your Most Vulnerable Assets
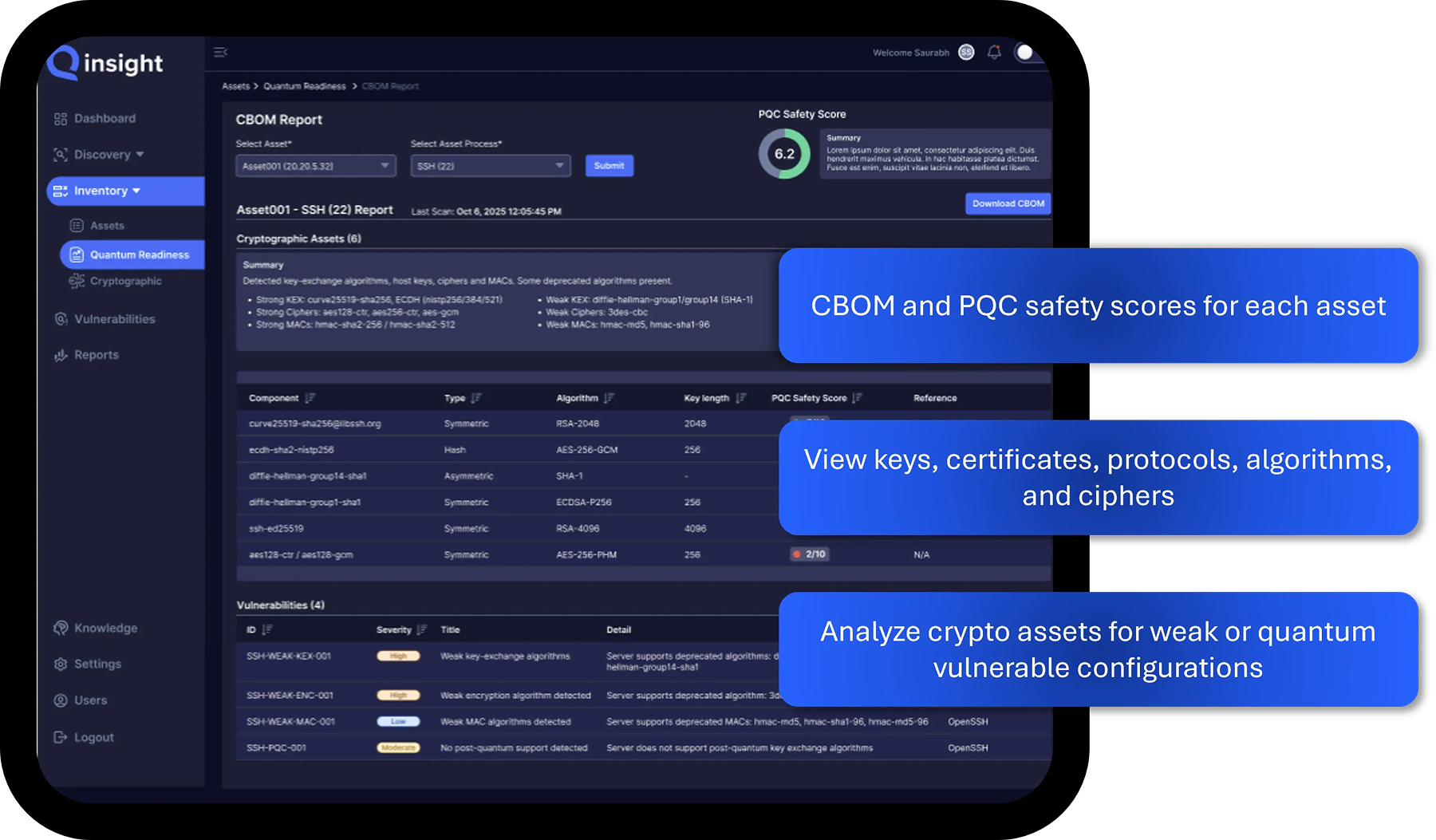
Analyze your cryptographic estate to ensure that algorithms, protocols, ciphers, certificates and key lengths are secure against cryptographically relevant quantum computers. Protect your most vulnerable assets with guided remediation workflows to migrate to NIST approved quantum-secure encryption.
Identify Quantum Risks
Keys & Keystores
Centralized record of all encryption keys and secure storage locations.
Certificates
Comprehensive inventory of digital certificates with issuer, algorithm and expiration details
Protocols
Catalog of cryptographic communication standards like TLS, SSH, and IPsec configurations.
Algorithms
List of encryption and hashing algorithms in use with associated security levels.
Libraries
Inventory of cryptographic software components and dependencies across applications and services.
Cipher Suites
Detailed mapping of protocol cipher combinations and their encryption strength or vulnerabilities.
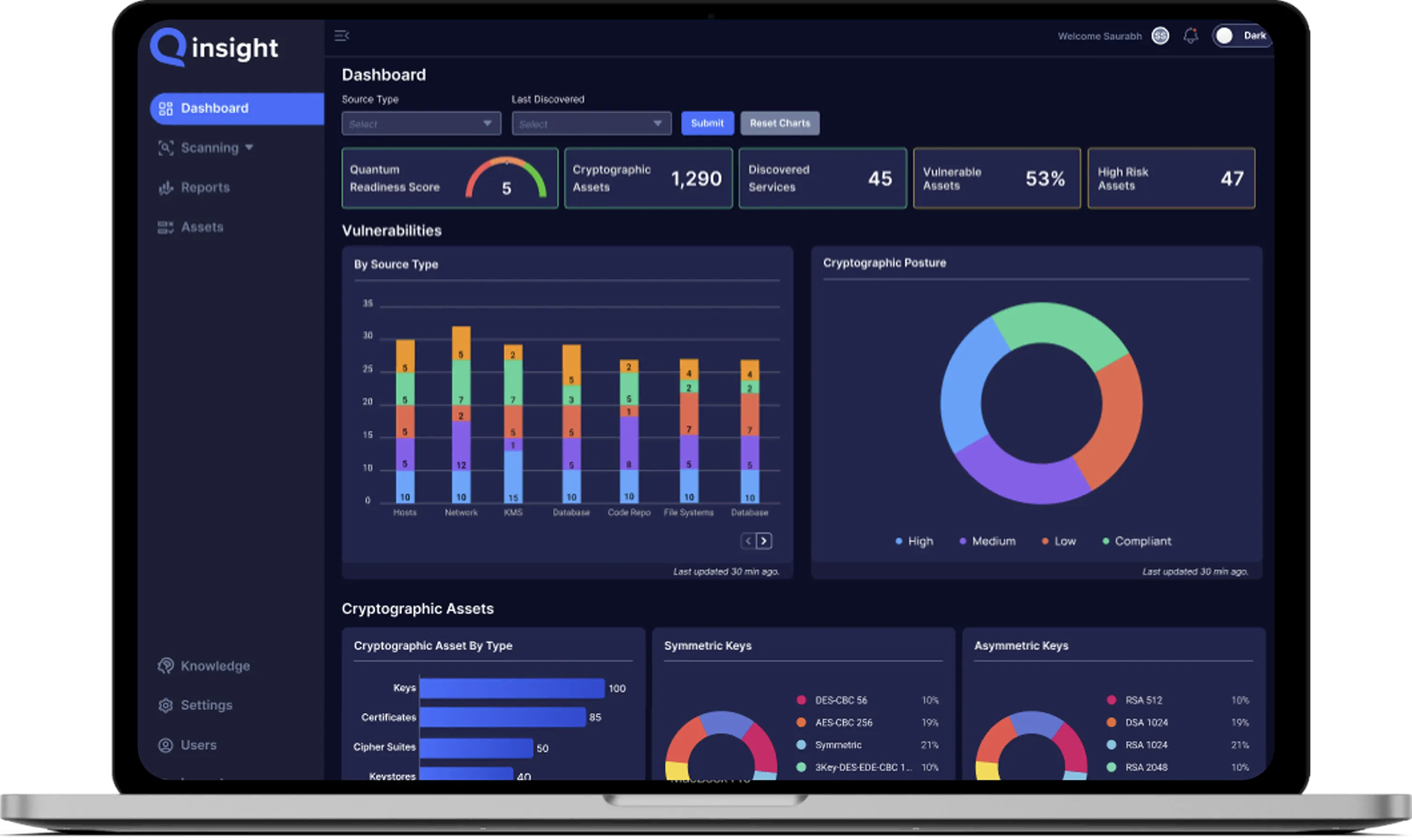
Who Needs a Cryptographic Inventory & Posture Management Platform?
CISOs and Security Architects
Get instant visibility into where encryption lives, what is implemented, and posture scoring so you can prioritize weak or misconfigured cryptography, conduct audits or create a roadmap and plan for PQC migration.
PKI & Crypto Governance Teams
Maintain a living inventory of algorithms and certificates, key/cert lifecycles, ciphers and protocols relevant to each data source. APIs provide flexibility and guided remediation instructions improve internal crypto-agility capabilities.
Compliance, risk and InfraSec leaders
Produce audit-ready reports and dashboards mapped to NIST / NSA PQC guidance, with continuous monitoring and audit logs that embed smoothly into existing compliance workflows.

Benefits of a Cryptographic Inventory
Enhanced Security
Identify and remediate weak or misconfigured cryptography before attackers exploit vulnerabilities.
Operational Efficiency
Centralize cryptographic management to streamline audits, updates and remediation workflows.
Regulatory Compliance
Maintain visibility and evidence to meet evolving data protection and PQC regulations such as CNSA 2.0.
Reduced Attack Surface
Eliminate unused, expired, or weak cryptographic assets that increase organizational exposure.
Industry Standards & Best Practices
Align encryption practices with NIST, NSA and sector-specific cryptographic security frameworks.
Quantum Readiness
Assess and plan migration from vulnerable algorithms to NIST-approved post-quantum standards.
