// Our Platform //
Qinsight Platform Overview
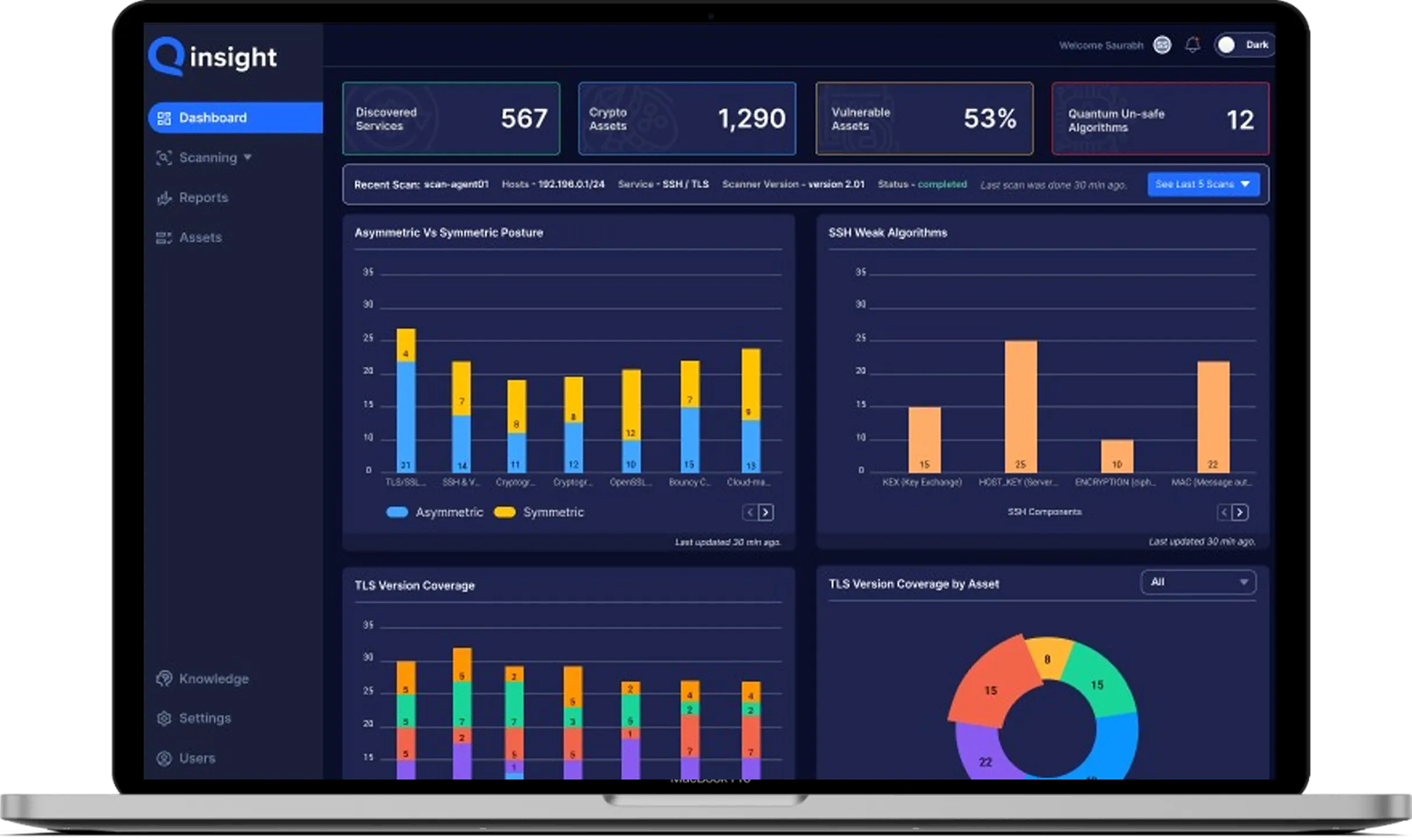
Qinsight is a cryptographic posture management platform that discovers, inventories, and analyzes all enterprise cryptography—keys, keystores, certificates, libraries, algorithms, protocols, and more. It surfaces weaknesses, compliance gaps, and quantum-vulnerable assets to improve organizations' quantum readiness.
How It Works
Qinsight helps you discover, inventory, analyze, and act on all enterprise cryptography in one place. It builds a living catalog of keys, X.509 certificates, algorithms, protocols, and owners (CBOM-ready), highlights weak or non-compliant crypto and quantum-vulnerable assets, and guides remediation to improve readiness.
// FAQ//
