Cryptographic Inventory: The Foundation of Digital Trust
A cryptographic inventory—a living, organization-wide map of keys, certificates, algorithms, libraries, protocols, policies, and usage

Most organizations can inventory their servers, apps, and software, yet few can list their cryptography. This visibility gap creates more than just technical debt, as it can lead to outages, compliance failures, and high-cost replacement cycles. More urgently, closing this gap is the prerequisite for post-quantum cryptography migration.
A cryptographic inventory is a living, organization-wide map of keys, certificates, algorithms, and policies. It is the backbone of risk management and quantum readiness. This guide outlines essential cryptographic inventory steps and how Qinsight simplifies the process of building a governed source of truth.
The evolution of cryptography: why inventory became mandatory
The post-quantum horizon and "Store Now, Decrypt Later" (SNDL) risks have bumped crypto governance to the top of the regulatory agenda. Discovery is merely the first step, and this is where cryptographic inventory comes in. But visibility isn’t enough; crypto data must be governed like any other Enterprise Risk Management (ERM) factor.
Cryptography wasn't designed for today’s sprawling, cloud-hybrid ecosystems. While protocols like TLS once served narrow e-commerce needs, they now underpin everything from the Internet of Things (IoT) to video conferencing. In this complex landscape, organizations can’t afford the liability of assuming their cryptography is fine as is. It's time to look beyond basic connectivity to identify where cryptography lives, evaluate its integrity, and verify its configuration.
A cryptographic inventory provides the comprehensive, cross-functional visibility required to effectively manage this risk. The output is a single “source of truth" that can be shared by security, infrastructure, and compliance teams to drive continuous risk reduction.
The Governance Imperative
Crypto management must be treated as critical infrastructure with clear ownership. A C-level owner (CISO/CIO) should be accountable for the program, while a centralized or federated team remains responsible for maintaining the "Golden Source of Cryptographic Inventory" (GSCI). By establishing this shared source of truth, incremental exposure can be quantified, and crypto risk can be prioritized alongside other enterprise risks.
The Five Domains of Coverage
A mature cryptographic inventory must capture more than just certificates to ensure no "blind spots" remain. A proper cryptographic inventory provides a comprehensive view across five essential domains:
- Operational: Configs and identity material in core infrastructure (on-prem and cloud), including mTLS, trust stores, and data-at-rest (databases and file systems).
- Software: Algorithms, libraries, and secrets embedded in applications, including CI/CD pipelines and code repositories where hardcoded keys often hide.
- Network: Negotiated characteristics for data-in-transit protocols like TLS, SSH, and IPsec.
- Managed: Lifecycle states and rotation policies in centralized key management tools (HSMs, KMSs, and Vaults).
- Hardware: Roots of Trust, TPMs, and cryptographic chips in IoT and edge modules.
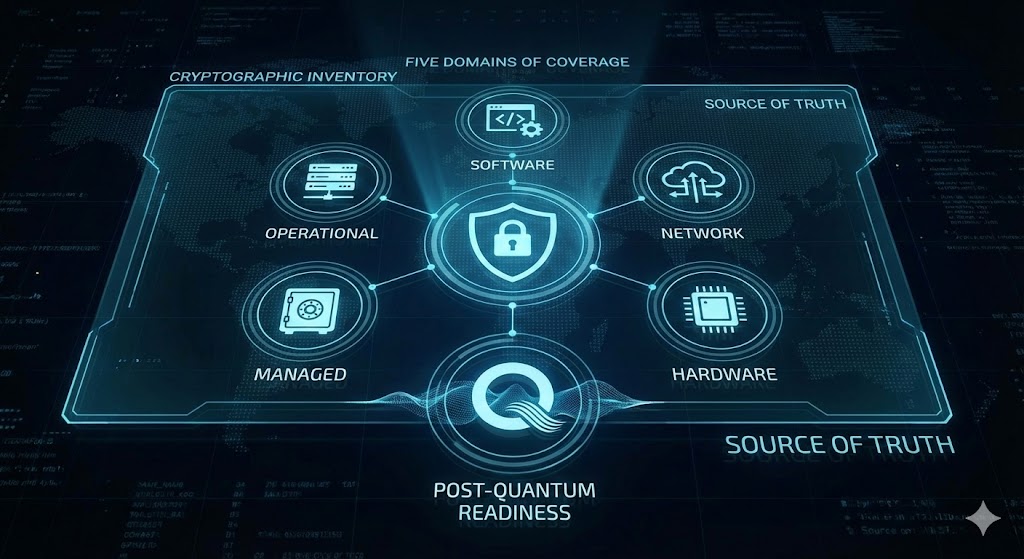
Why this matters: Many organizations only scan Network traffic, which leaves them blind to the "silent" cryptography embedded in Software (CI/CD/Code) and Operational storage (Databases). A true inventory must go deeper, scanning the entire estate to find dormant secrets and hardcoded keys that network scanners will always miss.
Differentiating CBOMs from Active Inventory
It's necessary to distinguish between a Cryptographic Bill of Materials (CBOM) and a full inventory. A CBOM acts like a Software Bill of Materials (SBOM), which lists capabilities, such as supported algorithms and libraries. While this is critical for vendor due diligence, a CBOM doesn’t detail how that software is actually provisioned or which cipher suites are enabled in specific environments. A cryptographic inventory expands CBOM utility by capturing real-world usage and enforcing policies even as infrastructure changes.
Tangible Applications for the CISO
When encryption is tracked properly, organizations can stop overspending on unnecessary tech and focus on repairing weak security.
Inventory can be utilized to drive these immediate outcomes:
- Compliance & Audit: Produce evidence on demand and map assets to specific controls for GDPR or PCI.
- Vulnerability Management: Link CVEs to affected endpoints or services and verify that fixes are successfully deployed.
- Crypto Agility: Coordinate rotations and algorithm transitions (including PQC) without breaking production systems.
- Secure Delivery: Automatically check your security settings with every software update to ensure no unintended or dangerous changes get through.
Get Cryptographic Visibility—Fast With Qinsight Atlas
Achieve the deep visibility required for post-quantum migration by automating inventory and scanning across your dynamic cryptographic estate. Qinsight’s platform leverages a sophisticated rules engine to analyze risk and prioritize remediation based on system criticality. This allows you to move from fragmented data to a governed, actionable security posture immediately.

Let’s turn cryptography from a black box into a managed, measurable asset.
Subscribe to our weekly newsletter
Receive weekly insights on cryptographic risks, emerging security standards and quantum readiness.



